
The types of technology used by financial institutions has grown in recent years, a trend that shows no signs of slowing down. At the same time, regulators want to ensure that banks continue investing in their information technology and information security environments to ensure they have robust controls.
Recently, executives and board members responding to Bank Director’s 2024 Risk Survey reported a heightened compliance environment, evidenced by more stringent examinations. Of the participants whose bank underwent a regulatory exam since March 2023, 30% said supervisors paid heightened attention to cybersecurity concerns; respondents weren’t asked about IT controls.
Information technology and information security risks are showing up in formal enforcement actions as well. Bank Director analyzed more than a dozen public consent orders that looked specifically at technology issues or identified issues at banks with complex financial technology partnerships from 2023 and 2024; those risks were a major focus of at least five of those actions.
“There is no way to eliminate risk,” says Justin Steffen, a partner in the financial institutions practice at Barack Ferrazzano Kirschbaum & Nagelberg who focuses on bank-fintech partnerships and regulatory matters. “I think the issue is, and what the orders are speaking to, is while there’s no way to eliminate risk, you need to do more to understand and address it.”
[This article is the fourth in a series about consent orders; you can read about Bank Secrecy Act and money laundering compliance here, third-party relationships here, and customer identification and due diligence here.]
Early-stage companies may not have as many resources or experience in the regulated financial services space, which can complicate their response to bank IT/IS control and audit expectations. These fintechs may not have SOC 2 exam findings or similar audit reports that banks have traditionally requested and relied on, says Steffen, leaving the bank to figure out a different way to assess the sophistication of their partner’s systems and otherwise hold that partner accountable throughout the relationship. A bank could require that partner to obtain a SOC 2 in a certain period of time. Establishing robust IT and cybersecurity audit rights, conducting audits at regular intervals and inquiring about the provider’s data sharing and privacy rules are other actions a bank could take.
It’s not an accident that IT/IS risk management overlaps with third-party vendor risk management. A control or process failure in one area could lead to control failures in another area, Steffen says. A bank may be unable to exercise its oversight function of fintech partners promptly and adequately because it’s not getting information from them in a timely fashion. The program agreement should include provisions that give the bank contractual safeguards so it can comply with Bank Secrecy Act/anti-money laundering laws and consumer compliance regulations.
But this applies to all vendor relations, not just fintech partnerships. Steffen points out that the 2014 Target Corp. hack that resulted in the breached credentials of roughly 110 million cards started with a compromised HVAC vendor. In 2023, the MoveIT breach compromised at least one core banking vendor, impacting some bank customers. However, in Bank Director’s 2024 Risk Survey, only 27% of respondents said their bank assessed cybersecurity practices for all vendors regardless of function, and 5% didn’t assess their vendors’ cybersecurity practices. Sixty-eight percent said they assessed cybersecurity practices for vendors in critical and high-risk functions. 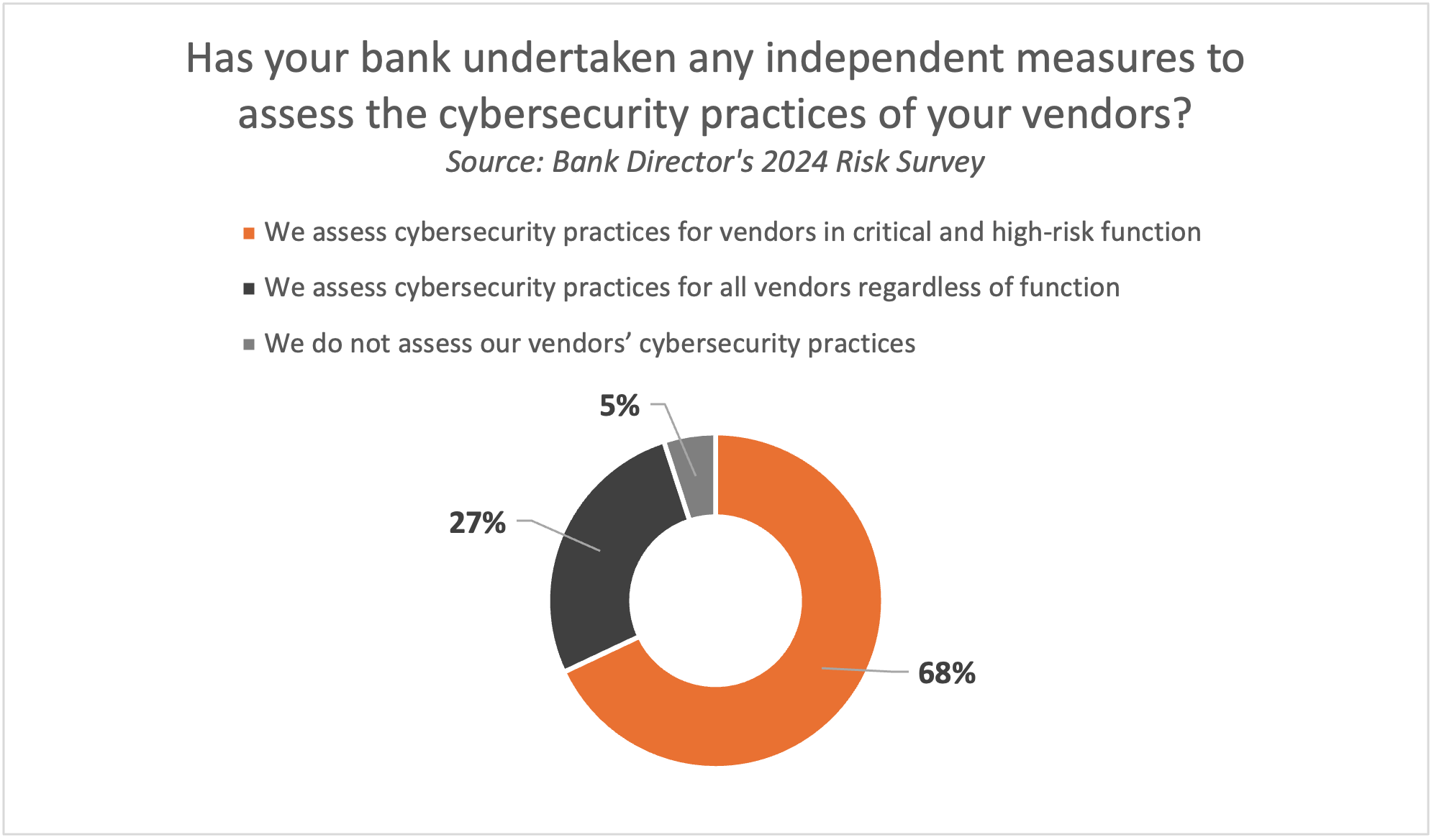 Data governance is another major challenge within the IT/IS space. Decentralization due to a proliferation of software used by different business lines — like customer relationship management and loan origination systems — has led to fragmentation of data, says Steve Gerschoffer, an internal audit technology principal at Crowe LLP consulting.
Data governance is another major challenge within the IT/IS space. Decentralization due to a proliferation of software used by different business lines — like customer relationship management and loan origination systems — has led to fragmentation of data, says Steve Gerschoffer, an internal audit technology principal at Crowe LLP consulting.
Some consent orders have required banks to build a data map, which can help a firm understand where its information is housed both within and outside the organization. Data maps can help banks comply with consumer privacy laws, manage the impact of a hack or recover from a natural disaster.
But implementing a data management and governance program is a “journey,” Gerschoffer says. It could take a bank a few years to locate, store, map and clean its data, though data analytics and artificial intelligence offer competitive advantages and efficiencies to banks that undertake that effort.
Another emerging area of examiner focus has been the control environment in bank cloud networks or storage, Gerschoffer says. Cloud technology remains a newer technology for some community banks, and they often “dabble” in them before embracing them, he says. But using the cloud still requires banks to establish risk management procedures, such as measurable controls that banks can test and document in an audit.
Gerschoffer points out that banks are increasingly reliant on technology to perform crucial tasks, and hackers and scammers are getting smarter and more creative at testing bank systems. Bank Director’s 2023 Technology Survey found that banks budgeted a median $1.5 million for technology last year; 83% of respondents said that represented an increase for their institution, at a median 10%. That steady climb could continue — or even accelerate — in future years, meaning that financial institutions can expect continued heightened scrutiny from regulators on IT/IS environments.
Information Technology, Security Takeaways From Formal Enforcement Actions:
• Bank IT audit programs should provide comprehensive and continuous coverage and be scoped to the findings of a comprehensive IT risk assessment. The IT audit program should identify the various types of IT audits and the frequency of them, including an independent IT general controls audit, penetration test and an annual vulnerability assessment. These assessments could increase in frequency if the bank makes significant IT changes.
• Smaller financial institutions may want to consider their staffing and in-house expertise, particularly if they’ve outsourced much of their IT needs in the past. One order directed a bank to retain an IT program manager or managers with relevant training, experience, knowledge of bank systems and applications and resources to manage its IT/IS.
• While a bank may choose to outsource some or all of its IT functions, that doesn’t negate the bank’s responsibility to have effective controls.
• Cybersecurity preparedness assessments and penetration testing can help banks identify, measure and document risks in their programs, grade their program’s maturity, close control gaps and remediate findings.

